WannaCry Ransomware Analysis and Decryption Methodolody
Today is a bad day. Shadowbroker leak of NSA’s exploits lead to weaponization of emails with MS17–010 the SMB vulnerability exploitation and delivery of Wanna Cry Ransomware. As I write this blog post, havoc is wrecked all over Europe and several entities have reported Wanna Cry infections and destruction of data, specially NHS in UK and entities in Spain.
I got hold of the ransomware sample (unfortunately not the delivery mechanism like the actual payload of exploit). Since I was short of time, I did a quick analysis, which might help IR teams with IOCs and YARA rules etc.

#Wanncary sample analyzed: MD5 84c82835a5d21bbcf75a61706d8ab549
Static Analysis
Strings found






Seems to be not packed and written in MSVC. However no Crypto API found in the IAT of binary:

Internal name of the ransomware is diskpart.exe, which is a MS utility for disk partitioning

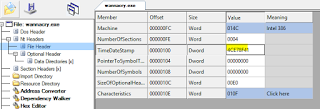
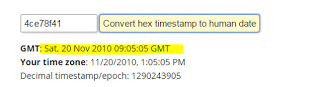
Date/Time of compilation (definitely tampered with)
One resource contains an archive file:
Dynamic Analysis
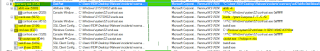
Process tree shows multiple process being spawned and batch and vbs script executions:
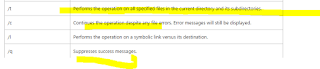
icacls command is used to grant access to Everyone using ACLs to the current working directory


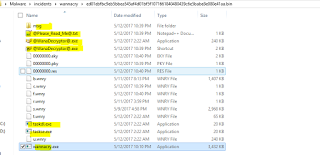
We can see msg folder created, which contains the Ransom note in various languages. We also see some other binaries created and the decryptor tool called “u.wnry” or “@WanaDecryptor@.exe”. A shortcut to the decryptor is also created for unknown reasons. The batch and vbs file execution is basically used to create this shortcut. We can also see two other binaries namely: taskdl.exe and taskse.exe. Some other files with extensions .eky and .pky most probably related to encryption.
We can see the ransome note in English

We can see addresses of the tor sites in c.wnry

s.wnry is the archive from the resource in the binary:

unzipping this archive file results in the following. This is the tor program:
3 more binaries dropped:

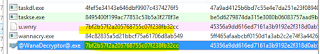
Hashes of the files:
taskdl.exe MD5: 4fef5e34143e646dbf9907c4374276f5
taskse.exe MD5: 8495400f199ac77853c53b5a3f278f3e
u.wnry MD5: 7bf2b57f2a205768755c07f238fb32cc (The decryptor tool)
WannaDecryptor@.exe MD5: 7bf2b57f2a205768755c07f238fb32cc (The decryptor tool)
Running the decryptor tool:

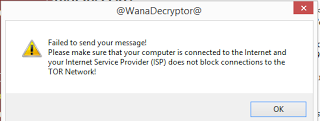
I tried clicking on the “Contact Us”, where we can enter text in a form and submit. If the internet conn fails then the following message is received. This confirms that the above tor sites are used by the decryptor to communicate
Some reg keys added:

After encryption the following message appears no the desktop:

I close the decryptor tool but the process keeps running and keeps popping up the decryptor window:

I tried running the other two dropped binaries as well. Notice their Description. SQL Client Configuration Utility EXE and “waitfor….”

The decryptor is spawning the tor exe taskhsvc.exe

Again the names/description of the files running as processes

Files are encrypted and extension of .WNCRYPT is added
Ransom note everywhere

Debugging
We can see the reg key being added

and the resource called “XIA” (CIA?) being loaded, which is an archive which contains everything from tor archive, ransom notes, decryptor tool, the other two binaries etc..
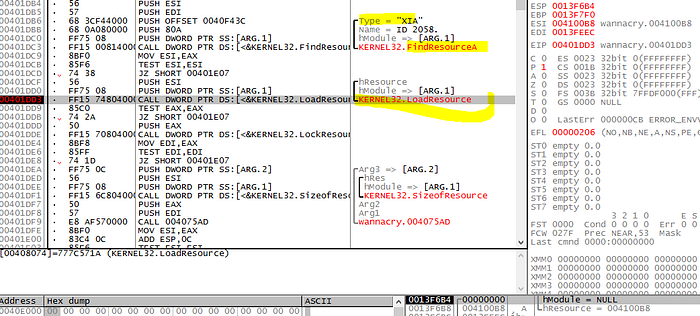
We can the files being created:

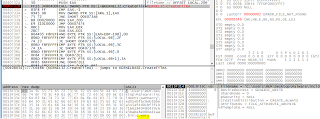
After writing all the files in the msg folder for ransomware note in different languages. It proceeds to write the decryptor tool:



You can see a small dot after attrib +h, indicating the ransomware is hiding the current folder by changing attribute to h:
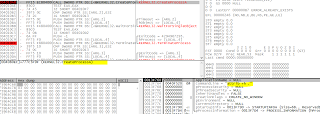
Hidden Now:

Also uses icacls.exe to grant full permission to Everyone current folder
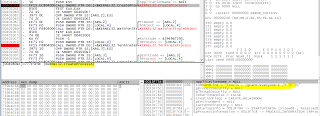
Next we see another file created called t.wnry with the header WANACRY!. No idea what this is

Next the malware allocated memory in memory and starts writing a binary there

Some libraries are loaded on runtime like kernel32, user32, advapi32.dll, shell32.dll, msvcrt.dll, msvcp60.dll, etc

The binary which was written to memory and then that memory area is made executable access using VirtualProtect:
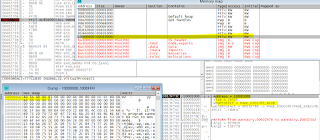
This is the beginning of the .text section (code)
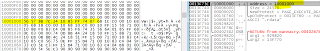
Now in memory map

I placed a hardware breakpoint on the start of text section, and henceforth the ransomware executes in memory. None of its code is “on-disk”


This in-memory code is actually the ransomware code


A lot of taskkill tasks so that the relevant processes can be killed and the files which are locked (database files etc) are released to be encrypted

Seems like it drops a file in C:\ root as well and makes it hidden and system file


Persistence mechanism:
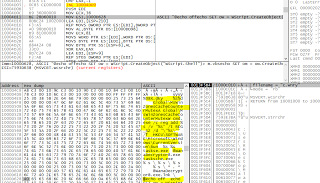
Also I see the batch script, which in turns create a vbs script, which is used to create a shortcut and is deleted then:
@echo off
echo SET ow = WScript.CreateObject(“WScript.Shell”)> m.vbs
echo SET om = ow.CreateShortcut(“%s%s”)>> m.vbs
echo om.TargetPath = “%s%s”>> m.vbs
echo om.Save>> m.vbs
cscript.exe //nologo m.vbs
del m.vbs
Some other interesting strings:
u.wnry%.1f BTC$%d worth of bitcoinwbr.wnryb.wnry attrib +h +s %C:\%s$RECYCLE%C:\%s$RECYCLE%s\hibsys%s :\taskdl.exe%s
f.wnryat cmd.exe /c start /b %s vs%s cotaskkill.exe /f /im mysqld.exetaskkill.exe /f /im sqlwriter.exetaskkill.exe /f /im sqlserver.exetaskkill.exe /f /im MSExchange*taskkill.exe /f /im Microsoft.Exchange.*%s fi%08X.eky%08X.pky%08X.res
Could this be the mutex created:

Reference to CryptoAPI routines

Some interesting strings:

“This folder protects against ransomware. Modifying it will reduce protection\Local Settings\Temp\AppData\Local\Temp\Program Files (x86)\Program Files\WINDOWS\ProgramData\Intel”
Upon execution we see that libraries are loaded on runtime and function calls made.
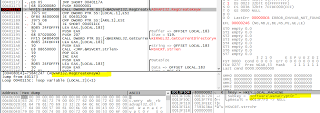
We can see the Import Address Table (IAT) being formulated:


Same thing with kernerl32.dll APIs, their addresses are also being stored in the memory-resident binary’s IAT:
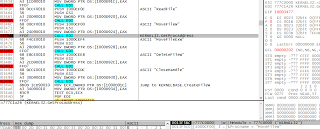
We can see that the malware wants to ensure it is running a single copy and it creates mutex:
Global\MSWinZonesCacheCounterMutexAO

We can see that access to everyone is granted to the Mutex
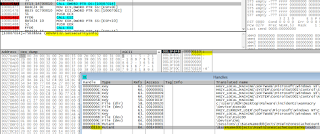
The CryptAcquireContext function is called to set the keys container and set up the CSP (Cryptographic Service Provider) to be used by the CryptoAPI for encryption of files:

WE can see the encryption key is being created:



We can see RSA encryption is used

Next we see key generation and we can see RSA 1024bit key will be generated
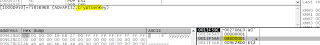

Next can see RSA key blob being encrypted with a session key
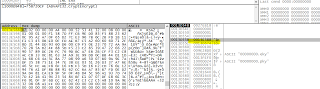
Post encryption (multiple rounds of encryption 5–6):
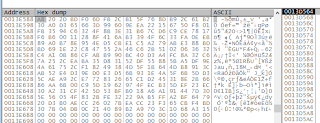


We can see attempt to create a new process:

The file does not exist so it copies from u.wnry to @WanaDecryptor@.exe

Next it runs the batch file to create the vbs to create the shortcut


After getting handle to shell folders like Desktop, the ransomware starts iterating through the files


Comparing the extension of the file it needs to encrypt

The file is a pcap and its being checked against all the file formats which Wanna Cry wants to encrypt
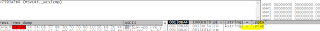
Various extensions which it looks for to encrypt:

Also checking if it is not an already encrypted file (encrypted by itself)

As soon as it find a file which matches the extension to be encrypted, it will encrypt it and move the original file to a new file name with extension “WNCYR”
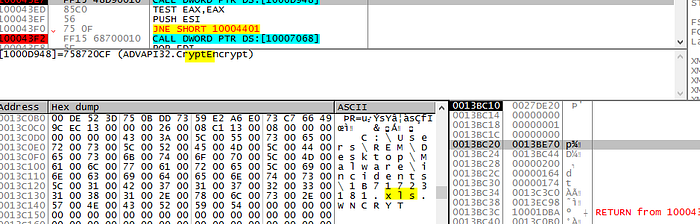
Moving the file

Then it deletes the temp file (the original file)
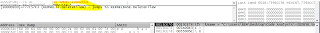
In between it spawns the taskdl.exe process
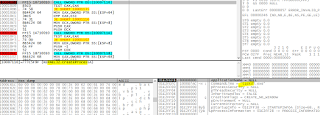
It looks for other logical drives to encrypt
I hope that this helps out. Thanks for reading

